Describe Botnets and Denial of Service Attacks
The malware is designed to enable the cyber criminal to make money off of the infected system such as harvesting key strokes using the infected systems to launch Denial of Service Attacks etc. Cron Cron is a Unix application that runs jobs for users and administrators at scheduled times of the day.
Attacks on Wi-Fi network is one common example that general people know.

. Describe how principles are applied to create ethical transparent and fair AI. In this blog post I will describe the common DDoS. Mobile security or more specifically mobile device security is the protection of smartphones tablets and laptops from threats associated with wireless computing.
DoS Symptoms and Tools. This behavior may be present in malware as well as in legitimate software. It has become increasingly important in mobile computingThe security of personal and business information now stored on smartphones is of particular concern.
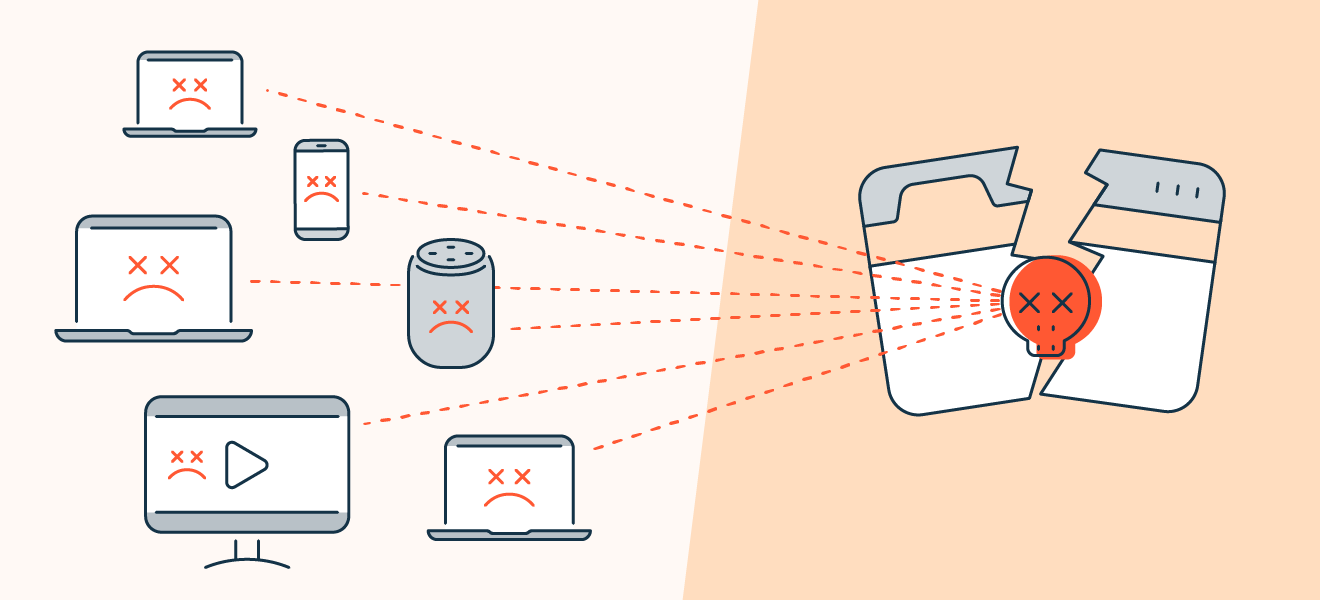
Denial-Of-Service Attack DOS. More and more users and businesses use smartphones. Attackers use Denial-of-Service DoS attack techniques in order to create denial-of-service on web servers.
For example by violating their privacy or endangering their devices security. Such attacks are used to make a point make some profit or simply for fun. Other such sub-types of wireless attacks are wireless authentication attack Encryption cracking etc.
Buffer Overflow Terminology and Background. Wireless attacks are malicious attacks done in wireless systems networks or devices. Through Secure Access Service Edge architecture and identify concepts required to recognize and potentially mitigate attacks against.
Configure and test a malware analysis security profile. Describe how bots and botnets are used to attack enterprise networks. A type of malware used by cyber criminals.
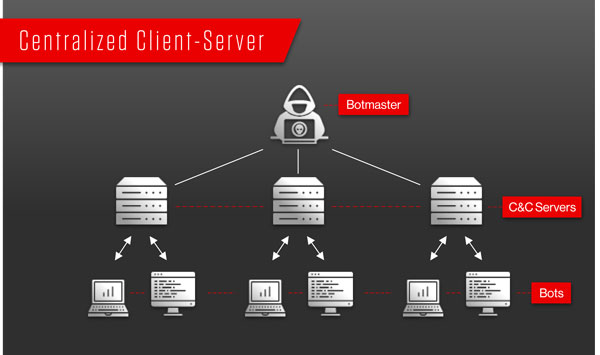
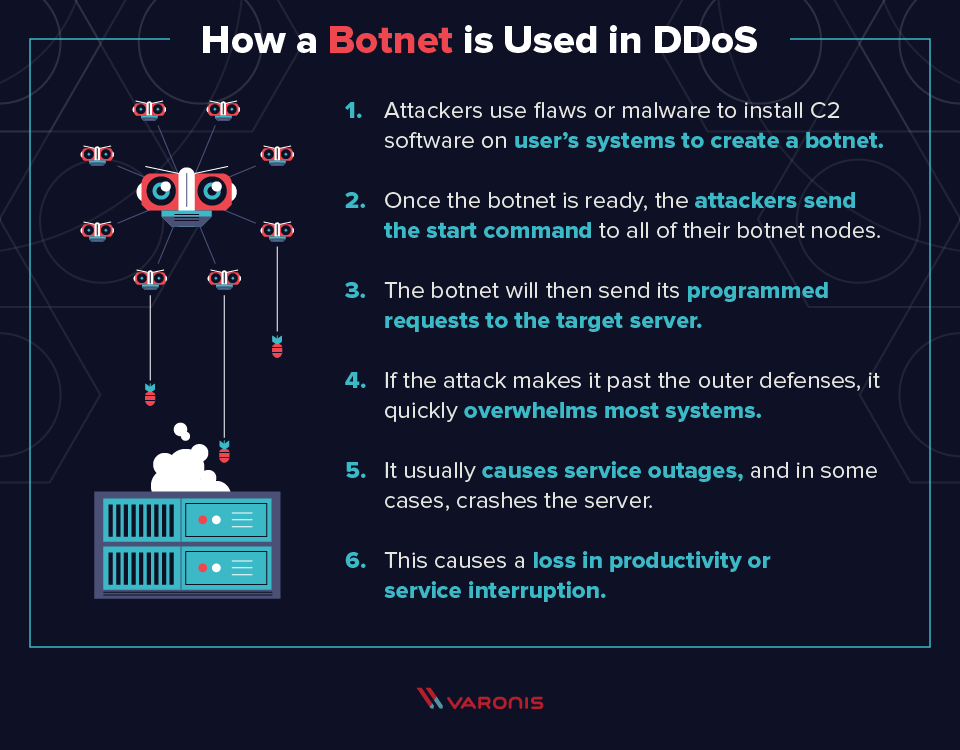
Categories of Denial of Service. Spamming and phishing attacks. Botnets and Disruption Attacks.
Spyware a portmanteau for spying software is software with malicious behavior that aims to gather information about a person or organization and send it to another entity in a way that harms the user.

Structure Of Distributed Denial Of Service Attack Download Scientific Diagram
A Simplified Model Of A Botnet Conducting A Ddos Attack Once An Army Download Scientific Diagram

What Is A Ddos Attack Cybernews
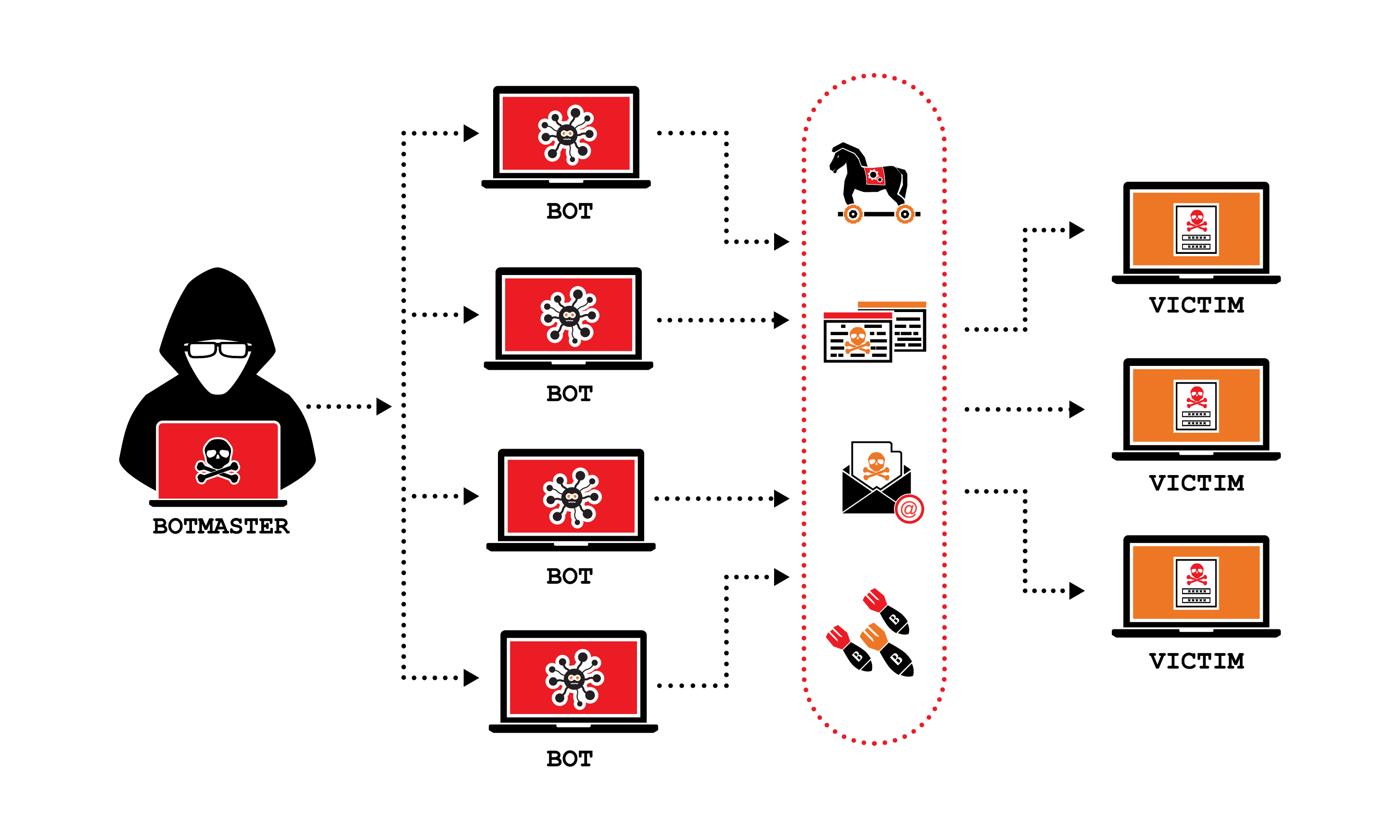
Ddos Attacks What Is A Ddos Attack What Does It Mean
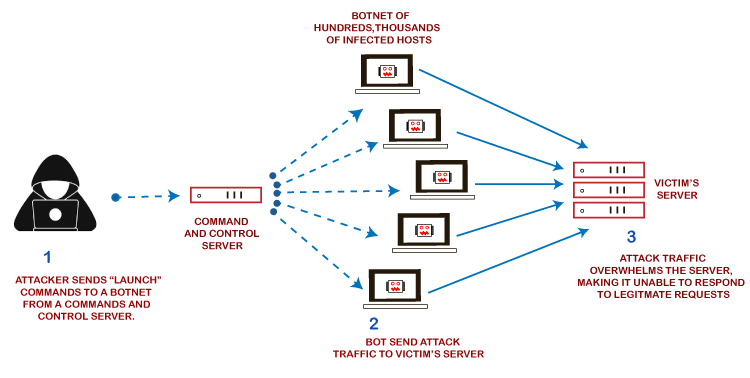
What Is Ddos Attack Javatpoint

Components Of Ddos Attack 34 Download Scientific Diagram

Mirai Botnet Operation And Communication Mirai Causes A Distributed Download Scientific Diagram

What Is A Botnet Kaspersky Daily Kaspersky Official Blog

Ddos Attack Model Of The Mobile Botnet Download Scientific Diagram
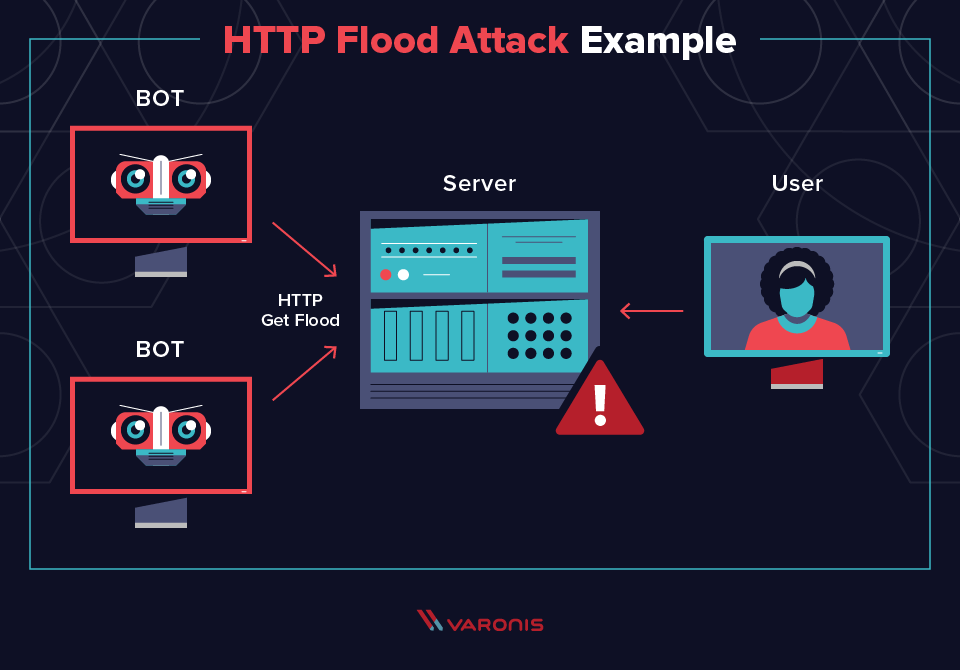
What Is A Ddos Attack Identifying Denial Of Service Attacks

What Is A Botnet Definition Types Example Attack

Ddos Attack By Using A Botnet 3 Download Scientific Diagram

The Mirai Botnet Malware Ddos Workflow Adapted From Level 3 Threat Download Scientific Diagram

What Is A Ddos Attack Identifying Denial Of Service Attacks
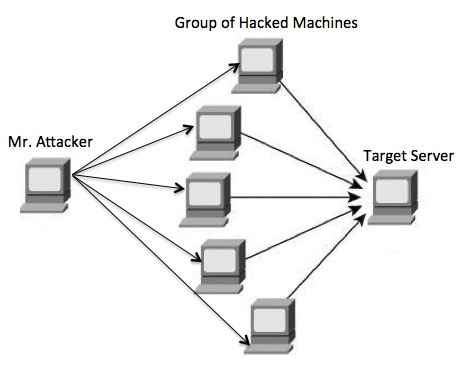


Comments
Post a Comment